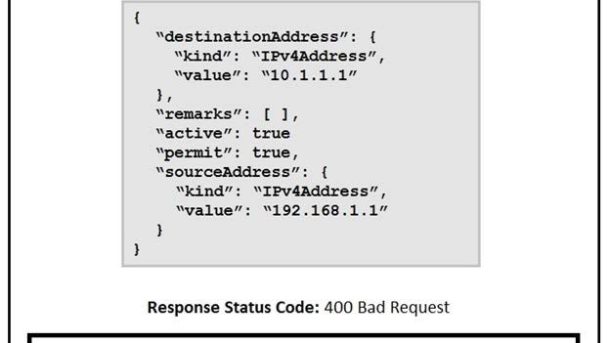
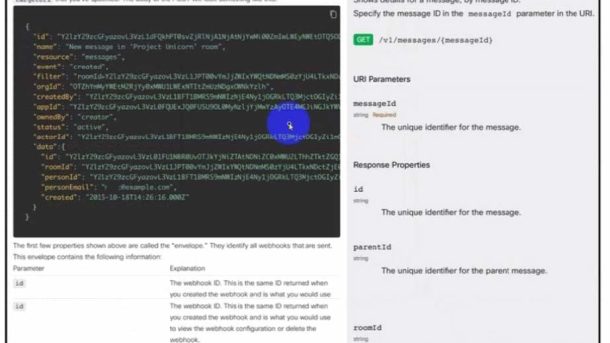
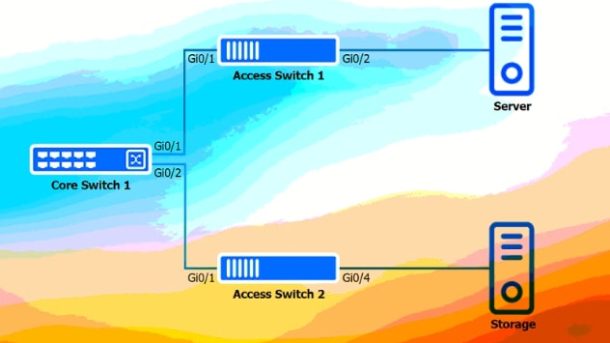
If you’re planning to design large-scale enterprise networks or pushing toward your CCNP Enterprise certification, the Cisco 300-420 ENSLD exam is a critical step.
In 2025, as software-defined technologies like SDA and model-driven telemetry continue to mature, having up-to-date preparation resources is more important than ever.
In this article, I will guide you through the latest Cisco 300-420 ENSLD dumps practice questions (https://www.leads4pass.com/300-420.html) and provide practical advice and test-taking strategies based on real-world experience.
» Read more about: Latest updated Cisco 300-420 practice questions and 300-420 dumps »
Continue reading...