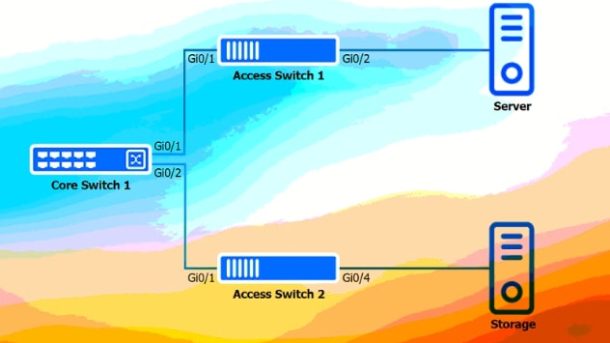
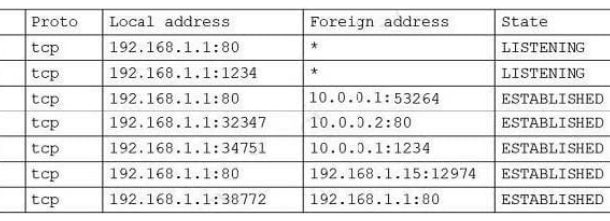
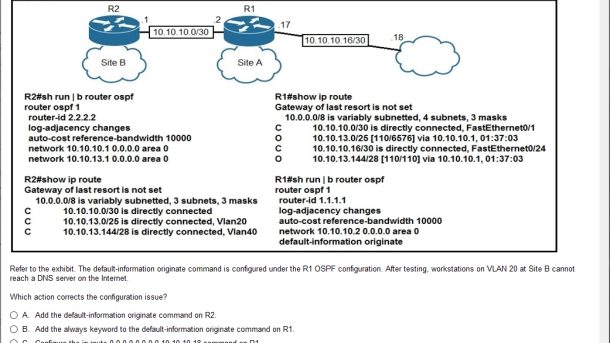
The CompTIA Network+ (N10-009) certification is a widely recognized credential in the IT industry, designed to validate professionals’ core skills in network configuration, troubleshooting, and security management. For candidates aiming to build a career in network administration, passing this certification is a critical step. However, the exam’s extensive content and complexity demand thorough preparation. Practice exam serve as valuable tools, helping candidates familiarize themselves with the exam format, identify knowledge gaps, and enhance test-taking skills.
This article aims to explore how to effectively utilize these resources and study efficiently to prepare for the CompTIA Network+ (N10-009) exam, helping candidates achieve their certification goals. More importantly, we are offering free access to a selection of the latest exam questions online for you to practice and enhance your test-taking skills.
» Read more about: CompTIA Network+ (N10-009) Practice Exam »
Continue reading...