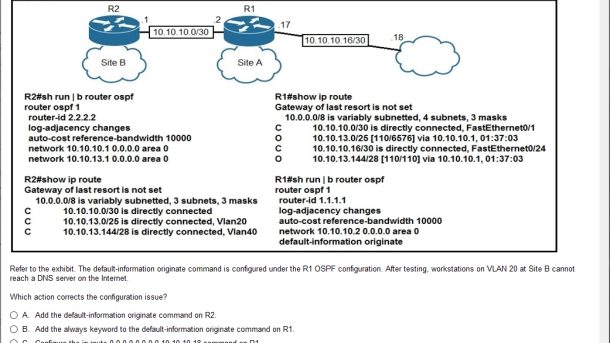
leads4pass has released the latest CCDP(“Cisco Certified DevNet Professional”)/CCDE(“Cisco Certified DevNet Expert”) 350-901 exam dumps, including 359 exam questions and answers, and all difficult problems analysis!
Moreover, leads4pass 350-901 dumps come with two exam study types: 350-901 dumps PDF, and 350-901 dumps VCE, both types contain the latest 350-901 exam questions that can help you pass the 350-901 DEVCOR successfully Certification exam!
» Read more about: Latest Leads4Pass CCDP/CCDE 350-901 Dumps with VCE and PDF & Online Practice »
Continue reading...