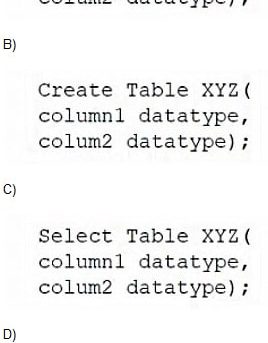
For everyone, using the valuable CompTIA DataSys+ DS0-001 practice exam questions can help you successfully pass the exam. I have been in the IT certification industry for more than 10 years. Based on past experience, I can provide you with real-time updates and good privacy. Exam materials are the most effective materials that really help you.

Pass4itsure CompTIA DataSys+ DS0-001 practice exam questions are updated in real-time and are private real exam materials. Currently, 93 of the latest exam questions and answers have been updated. You can visit Pass4itsure to download the complete CompTIA DataSys+ DS0-001 practice exam questions and Answer.
» Read more about: CompTIA DataSys+ DS0-001 Practice Exam Questions and Answers »
Continue reading...