How do I pass the Microsoft MCSE 70-744 exam?
Passing the first exam with Microsoft 70-744 is not an easy task!
Follow Examscode Microsoft Blog! Share the latest and most effective exam tips for free.
Examscode shares the latest exam questions and answers throughout the year.
Microsoft 70-744 exam “Securing Windows Server 2016”.
Examscode shares the latest Microsoft 70-744 exam pdf, 70-744 exam practice questions, the latest questions to help you improve your exam pass rate!
We prepared the Microsoft 70-744 highest exam pass secret, 70-744 Dumps. https://www.leads4pass.com/70-744.html The latest and most complete Microsoft 70-744 exam dump.
Examscode 70-744 exam catalog
- Latest Microsoft 70-744 youtube
- Latest Microsoft 70-744 google drive
- Latest Microsoft 70-744 Exam Practice
- Latest Microsoft 70-744 coupon code 2020
- leads4pass Reviews 2020
Examscode Microsoft 70-744 video tutorial
Latest Microsoft 70-744 exam pdf free download
[PDF Q1-Q12] Free Microsoft 70-744 pdf dumps download from Google Drive: https://drive.google.com/file/d/1ovlacBpye_-mX7K19yzKrAPeetgtQ5r2
Exam 70-744: Securing Windows Server 2016: https://docs.microsoft.com/en-us/learn/certifications/exams/70-744
Candidates for this exam secure Windows Server 2016 environments. Candidates are familiar with the methods and technologies used to harden server environments and secure virtual machine infrastructures using Shielded and encryption-supported virtual machines and Guarded Fabric.
Candidates manage the protection of Active Directory and Identity infrastructures and manage privileged identities using Just in Time (JIT) and Just Enough Administration (JEA) approaches, as well as implement Privileged Access Workstations (PAWs) and secure servers using the Local Administrator Password Solution (LAPS).
Candidates should also be able to use threat detection solutions such as auditing access, implementing Advanced Threat Analytics (ATA), deploying Operations Management Suite (OMS) solutions, and identifying solutions for specific workloads.
Skills measured Microsoft 2020
- Implement Server Hardening Solutions (25-30%)
- Secure a Virtualization Infrastructure (5-10%)
- Secure a Network Infrastructure (10-15%)
- Manage Privileged Identities (25-30%)
- Implement Threat Detection Solutions (15-20%)
- Implement Workload-Specific Security (5-10%)
Latest Updates Microsoft 70-744 Exam Practice Questions and Answers
QUESTION 1
You have a Host Guardian Service (HGS) and a guarded host.
You have a VHDX file that contains an image of Windows Server 2016.
You need to provision a virtual machine by using a shielded template.
Which three files should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. a TPM baseline policy file
B. a TPM identifier file
C. a shielding data .pdk file
D. a signature for the .vhdx file
E. an unattended.xml file
Correct Answer: CDE
https://docs.microsoft.com/en-us/windows-server/security/guarded-fabric-shielded-vm/guarded-fabric-create-a-shieldedvm-template https://docs.microsoft.com/en-us/windows-server/security/guarded-fabric-shielded-vm/guarded-fabrictenantcreates-shielding-data
QUESTION 2
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1
that runs Windows Server 2016.
You deploy Advanced Threat Analytics (ATA) to Server 1.
you need to move the ATA database to a different folder.
A. Config.json
B. Config.xml
C. Mongod.cfg
D. Web.config
Correct Answer: B
QUESTION 3
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as
shown in the following table.
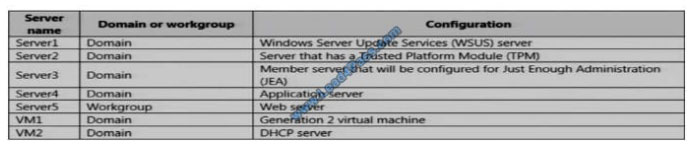
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker). You have an organizational unit (OU) named
OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of computers in the marketing department.
A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1.
You create an update rule named Update1.
You need to ensure that AppLocker rules will apply to the marketing department computers. What should you do?
A. From the properties of OU2, modify the Security settings.
B. In GP2, configure the Startup type for the Application Identity service.
C. From the properties of OU2, modify the COM+ partition Set
D. In GP2, configure the Startup type for the Application Management service.
Correct Answer: B
https://docs.microsoft.com/en-us/windows/device-security/applocker/configure-the-application-identity-service Because
AppLocker uses this service “Application Identity” to verify the attributes of a file, you must configure it to start
automatically in at least one Group Policy object (GPO) that applies AppLocker rules.
QUESTION 4
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one
correct solution, while others might not have a correct solution.
After you answer a question in these sections, you will NOT be able to return to it. As a result, these questions will not
appear on the review screen.
You deploy Windows Server 2016 to a server named Server1. You need to ensure that you can run Windows Containers on Server1.
Solution: On Server1, you enable the Containers feature, and then you restart the server.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
QUESTION 5
You have a Hyper-V host named Server1 that runs Windows Server 2016. Server1 has a generation 2 virtual machine
named VM1 that runs Windows 10.
You need to ensure that you can turn on BitLocker Drive Encryption (BitLocker) for drive C: on VM1. What should you
do?
A. From Server1, install the BitLocker feature.
B. From Server1, enable nested virtualization for VM1.
C. From VM1, configure the Require additional authentication at startup Group Policy setting.
D. From VM1, configure the Enforce drive encryption type on fixed data drives the Group Policy setting.
Correct Answer: C
https://www.howtogeek.com/howto/6229/how-to-use-bitlocker-on-drives-without-tpm/If you don\’t use TPM for
protecting a drive, there is no such Virtual TPM or VM Generation, or VM Configurationversion requirement, you can
even use Bitlockerwithout TPM Protector with earlier versions of Windows. How to Use BitLocker Without a TPMYou can
bypass this limitation through a Group Policy change. If your PC is joined to a business or school domain, you can\’t
change the Group Policy setting yourself. Group policy is configured centrally by your network administrator. To open the
Local Group Policy Editor, press Windows+R on your keyboard, type “gpedit.msc” into the Rundialog box, and press
Enter.Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > WindowsComponents BitLocker Drive Encryption > OperatingSystem Drives in the left pane.
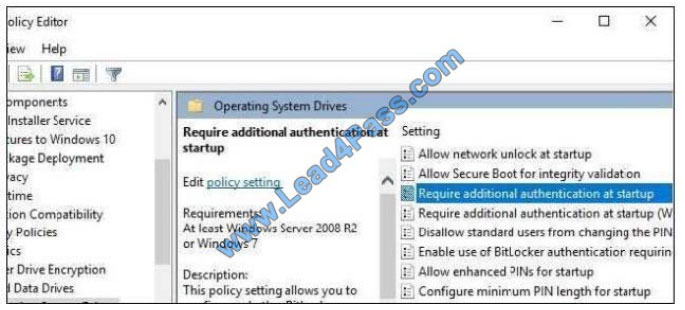
Double-click the “Require additional authentication at startup” option in the right pane.
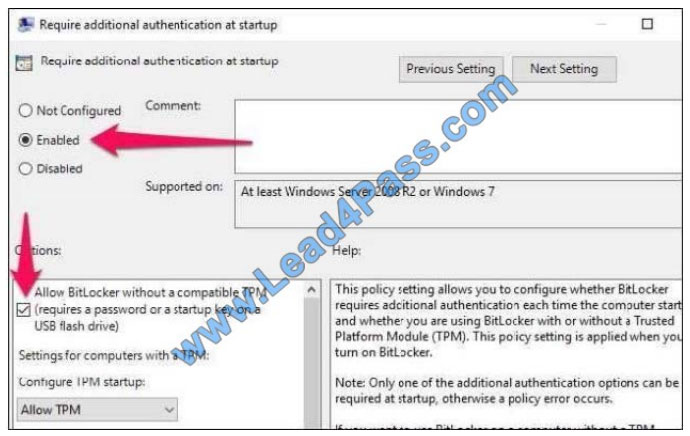
Select “Enabled” at the top of the window, and ensure the “Allow BitLocker without a compatible TPM (requires a
password or a startup key on a USB flash drive)” checkbox is enabled here. Click “OK” to save your changes. You can
now close the Group Policy Editor window. Your change takes effect immediately–you don\’t even need to reboot.
QUESTION 6
Your network contains an Active Directory domain named contoso.com.
The domain contains two global groups named Group1 and Group2. A user named User1 is a member of Group1
You have an organizational unit (OU) named OU1 that contains the computer accounts of computers that contain
sensitive data. A Group Policy object (GPO) named GPO1 is linked to OU1. OU1 contains a computer account named
Computer1.
GPO1 has the User Rights Assignment configured as shown in the following table.

You need to prevent User1 from signing in to Computer1. What should you do?
A. From Default Domain Policy, modify the Allow log on local user right
B. On Computer1, modify the Deny log on locally user right.
C. From Default Domain Policy, modify the Deny log on local user right
D. Remove User1 to Group2.
Correct Answer: D
https://technet.microsoft.com/en-us/library/cc957048.aspx”Deny log on locally”Computer Configuration\Windows
Settings\Security Settings\Local Policies\User Rights AssignmentDetermines which users are prevented from logging
on at the computer. This policy setting supersedes the Allow Log on local policy setting if an account is subject to
both policies. Therefore, adding User1 to Group2 will let User1 inherit both policies, and then prevent User1 to sign in
toComputer1.
QUESTION 7
HOTSPOT
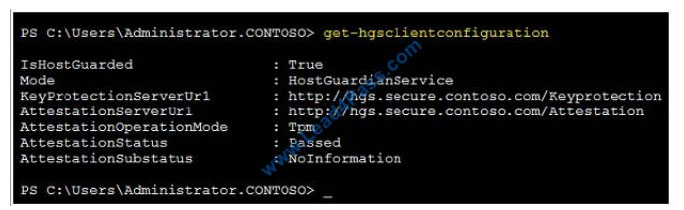
You run the Windows PowerShell commands as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the graphic.
NOTE: Each correct selection is worth one point. Hot Area:
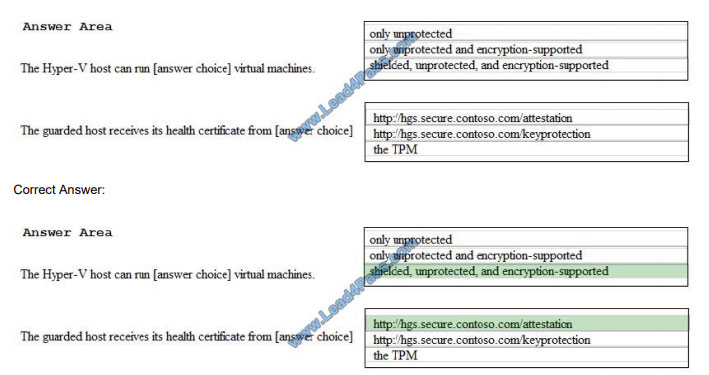
References: https://blogs.technet.microsoft.com/datacentersecurity/2016/03/16/windows-server-2016-and-host-guardianservice-for-shielded-vms/ https://docs.microsoft.com/en-us/windows-server/security/guarded-fabric-shieldedvm/guarded-fabric-troubleshoot-hgs
QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains a user named User1 and
a computer named Computer1. Remote Server Administration Tools (RSAT) is installed on Computer1.
You need to add User1 as a data recovery agent in the domain.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to
the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
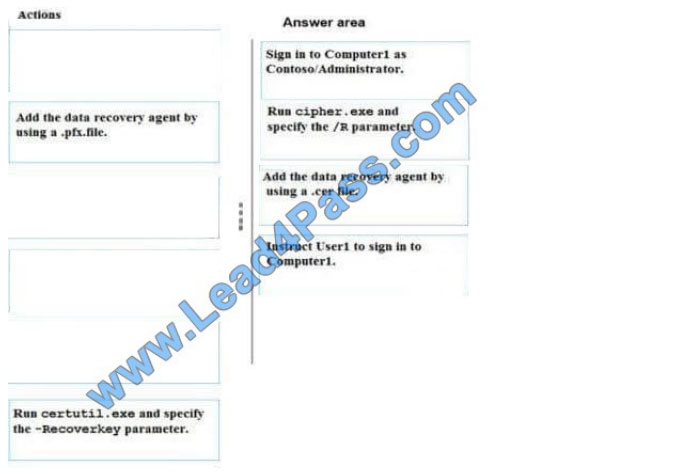
References: https://msdn.microsoft.com/library/cc875821.aspx#EJAA https://www.serverbrain.org/managingsecurity-2003/using-the-cipher-command-to-add-data-recovery-agent.html
QUESTION 9
Your network contains an Active Directory domain named contoso.com. The domain contains servers that run
Windows Server 2016.
You enable Remote Credential Guard on a server named Server1.
You have an administrative computer named Computer1 that runs Windows 10.
Computer1 is configured to require Remote Credential Guard.
You sign in to Computer1 as Contoso\User1.
You need to establish a Remote Desktop session to Server1 as Contoso\ServerAdmin1.
What should you do first?
A. Install the Universal Windows Platform (UWP) Remote Desktop application
B. Turn on virtualization-based security
C. Run the mstsc.exe /remote guard
D. Sign in to Computer1 as Contoso\ServerAdmin1
Correct Answer: D
When Computer1 is configured to require Remote Credential Guard, you cannot use NTLM authentication to specify (or
impersonate) another user account when connecting to Server1. Therefore, you have to sign in to Computer1 as
“ServerAdmin1” and use Kerberos for authenticating to RDP server “Server1” when Remote Credential Guard is
required.
QUESTION 10
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as
shown in the following table.
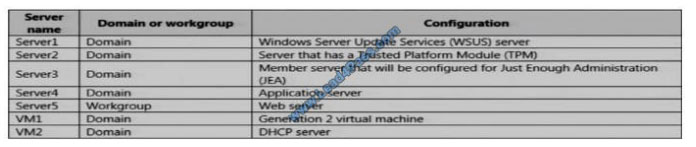
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker).You have an organizational unit (OU) named
OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of the computers in the marketing department.
A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1.
You create an update rule named Update1.
You need to ensure that you can view Windows PowerShell code that was generated dynamically and executed on the
computers in OU1.
What would you configure in GP1?
A. Object Access\Audit Application Generated from the advanced audit policy
B. Turn on PowerShell Script Block Logging from the PowerShell settings
C. Turn on Module Logging from the PowerShell settings
D. Object Access\Audit Other Object Access Events from the advanced audit policy
Correct Answer: B
https://docs.microsoft.com/en-us/powershell/wmf/5.0/audit_scriptWhile Windows PowerShell already has the
LogPipelineExecutionDetails Group Policy setting to log the invocation of cmdlets, PowerShell\’s scripting language
has plenty of features that you might want to log and/or audit. The new Detailed Script Tracing feature lets you enable
detailed tracking and analysis of Windows PowerShell scripting use on a system. After you enable detailed script tracing,
Windows PowerShell logs all script blocks to the ETW event log, Microsoft-Windows-PowerShell/Operational. If a script
block creates another script block (for example, a script that calls the Invoke-Expression cmdlet on a string), that
resulting script block is logged as well. Logging of these events can be enabled through the Turn on PowerShell Script
Block Logging Group Policysetting (in Administrative Templates -> WindowsComponents -> Windows PowerShell).
QUESTION 11
Your network contains an Active Directory named contoso.com.
The domain contains the computers configured as shown in the following table.
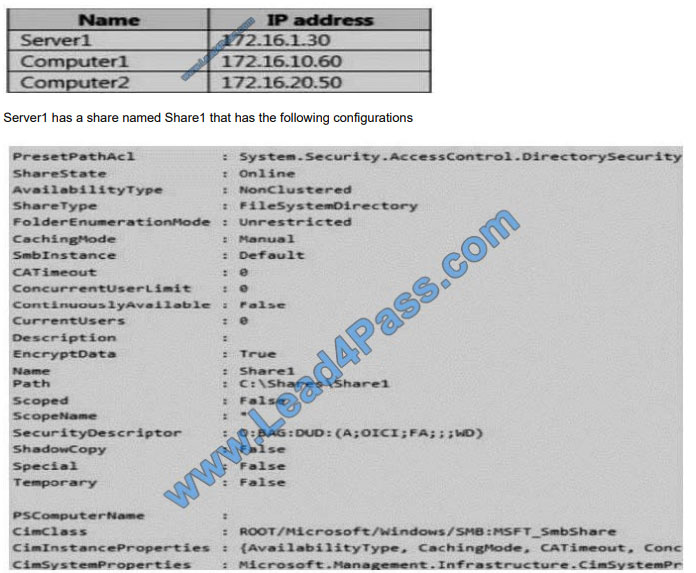
Server1, Computer1, and Computer2 have the connection security rules configured as shown in follow:
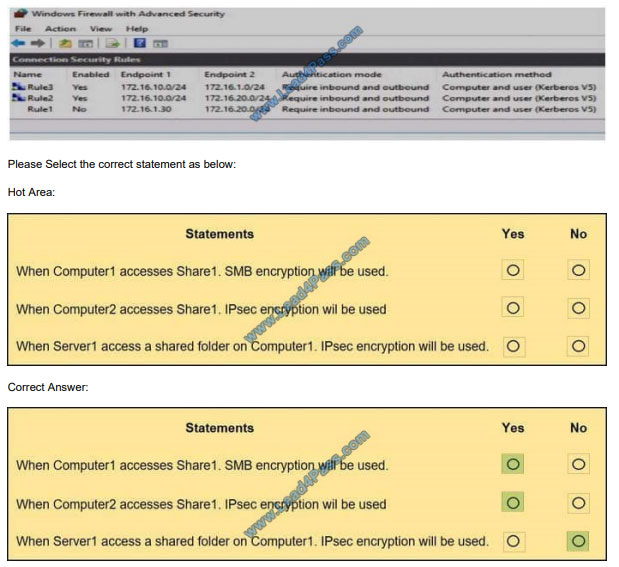
When Computer1 accesses Share1, SMB encryption will be used: YES When Computer2 accesses Share1, SMB
encryption will be used: YES When Server1 accesses a shared folder on Computer1, IPsec encryption will be used: NO
The shared folder “Share1” is configured with “EncryptData: True”, no matter which network the client resides, SMB 3
communication will be encrypted. When Server1 access Computer1 over the network, the original packet L3 IP Header is
as
follow -172.16.1.30? gt; 172.16.10.60These traffic does not match the enabled IPSec rule “Rule2” nor “Rule3”, and the
only matching rule “Rule1” is disabled. So, no IPsec encryption will be achieved.
QUESTION 12
Your network contains an Active Directory domain named contoso.com. You plan to implement encryption on a file
server named Server1. Server1 has TPM 2.0 and uses Secure Boot Server1 has the volumes configured as shown in
the
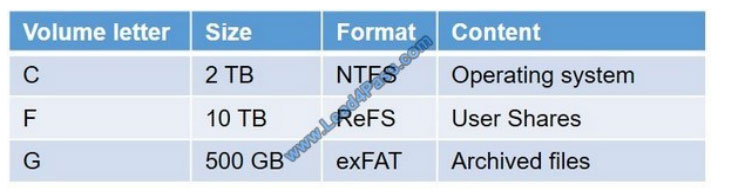
following table.
You need to encrypt the contents of volumes C and G. The solution must use the highest level of security possible.
What should you use to encrypt the contents of each volume? To answer, drag the appropriate encryption options to the
correct volumes. Each encryption option may be used once, more than once, or not at all. You may need to drag the
split
bar between panes or scroll to view content.
Select and Place:
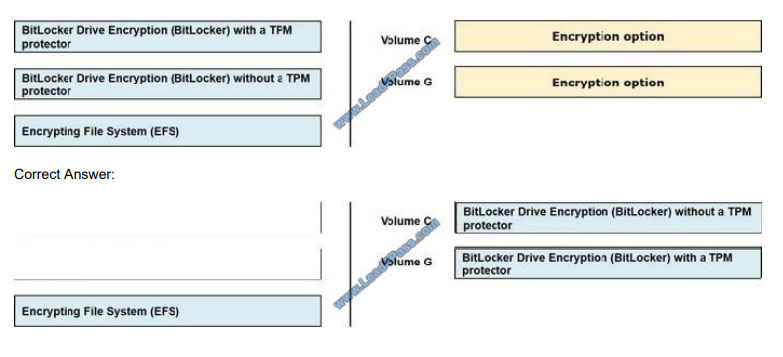
QUESTION 13
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named
Server1 that runs Windows Server 2016.Server1 has a shared folder named Share1.
You plan to create a subfolder in Share1 for each domain user.
You need to limit each user to use 100 MB of data in their respective subfolder.
The solution must enable the users to be notified when they use 80 percent of the available space in the subfolder.
Which tool should you use?
A. File Explorer
B. Shared Folders
C. Server Manager
D. Disk Management
E. Storage Explorer
F. Computer Management
G. System Configuration
H. File Server Resource Manager (FSRM)
Correct Answer: H
Share lead4Pass Microsoft 70-744 Coupon codes 2020

About leads4pass
leads4pass collaborates with several free blogs to share the latest effective exam exercise questions to help more people easily improve
their exam skills and experience. leads4pass.com available(the most accurate IT exam study materials, 100% money back guarantee,
professional assistant, 100% Reliable!)

Microsoft 70-744 Exam Tips Summary:
Microsoft 70-744 Exam Tips Summary:
ExamsCode freely shares Microsoft 70-744 exam dumps, 70-744 exam practice questions, 70-744 youtube video learning, 70-744 pdf,
and official updates hope to help you successfully pass the exam!
Good luck!
ps.
1.Latest update leads4pass 70-744 exam dumps:
https://www.leads4pass.com/70-744.html (258 Q&As)
2.[Q1-Q12 PDF] Free Microsoft 70-744 pdf dumps download from Google Drive:
https://drive.google.com/file/d/1ovlacBpye_-mX7K19yzKrAPeetgtQ5r2
Good luck!


